Access Management is a must-have for data security, it offers a laser-focused approach to who sees what and when. Enter Folderit’s advanced granular access management—with features designed to revolutionize how organizations handle their digital assets.
What is Granular Access Management?
Granular Access Management is the fine-tuning of permissions, ensuring that users have access only to the specific data they need. Instead of broad permissions that grant access to large data sets, granular permissions focus on detailed, specific access.
With the digital landscape becoming more complex, the need for precise access management has risen significantly. As such Folderit’s DMS provides a solution.
Enter Folderit’s Custom Permission Levels
Folderit recognizes the diverse needs of modern organizations. Hence, it offers custom permission levels, allowing administrators to define access down to the minutest detail. Whether it’s viewing a file, editing it, or just seeing the file name without accessing its content, Folderit’s custom permissions have it covered. These permissions are part of Folderit’s Tailor plan, ensuring that organizations get a bespoke experience tailored to their unique needs.
How Folderit’s Custom Permissions Work
Folderit’s custom permission levels are designed with both simplicity and sophistication in mind. Here’s a breakdown of how it works:
- Role Definition: Administrators can define roles based on job functions or project requirements. Each role can have its unique set of permissions.
- Granular Permissions: Within each role, permissions can be set at a very granular level. For instance, a role can be given permission to view file names but not access the actual files. This is especially useful for overview roles where individuals need to understand what data exists without actually interacting with the content.
- Toggle Features: One of the standout features is the ability to toggle specific functionalities on or off. For instance, the audit trail, which logs every interaction with the data, can be made visible or hidden based on the role’s permissions.
- Integration with Other Features: The custom permission levels seamlessly integrate with other Folderit features. For example, when combined with Folderit’s tag-based access, it offers an unparalleled level of access control.
Example Use Cases and Practical Applications of Folderit’s Custom Permissions
Project Management Oversight:
- Scenario: A project manager needs to monitor the progress of various projects without altering the content.
- Application: Grant the manager permission to view file and folder names, but restrict them from modifying or downloading the actual content.
External Auditors:
- Scenario: An external audit firm requires access to specific financial documents without altering them.
- Application: Provide auditors with read-only access to relevant folders and files, and enable the audit trail feature so they can view the document interaction history.
Collaborative Workspaces:
- Scenario: A team collaborates on a project where members have different roles – designers, writers, and editors.
- Application: Designers can add and preview files, writers can create and update files, while editors have full access to read, update, and approve changes.
Client Portfolios:
- Scenario: A financial advisor manages portfolios for multiple clients and wants to share specific documents with each client without exposing other clients’ data.
- Application: Use Folderit’s custom permissions to share specific folders with individual clients, ensuring data privacy and confidentiality.
Research and Development:
- Scenario: An R&D team is working on a confidential project. They need to share data with the marketing team but want to restrict certain sensitive information.
- Application: Grant the marketing team access to view general project folders but restrict access to folders containing proprietary research.
Educational Institutions:
- Scenario: A university wants to share course materials with students but restricts them from altering or uploading content.
- Application: Provide students with permissions to view and download course files but prevent them from making modifications or additions.
Legal Firms:
- Scenario: A law firm needs to share case files with clients, allowing them to view but not alter the original documents.
- Application: Use custom permissions to share specific case files with clients, ensuring they can view and comment but not modify the original content.
By utilizing Folderit’s Custom Permissions, organizations can tailor access to their specific needs, ensuring data integrity, security, and efficient collaboration.
A Deeper Dive into Folderit’s Granular Access Management and Custom Permissions for Users
Here’s a deep dive into our granular access management for users:
1. Granular Organization-Level Permissions:
- Account Management: Users can be granted specific permissions to read or update account details. This ensures that only authorized personnel can make changes to critical account settings.
- Admin Tools: Control is extended to those who can add new admins, download comprehensive data, and access detailed reports & dashboards.
2. In-Depth Folder Permissions:
- Visibility & Creation: Decide who can see folders, create new ones, or even duplicate existing folders. This is crucial for maintaining a structured data hierarchy.
- Movement & Sharing: Control over moving folders ensures data integrity. Additionally, folders can be shared with specific users or even via a public link for broader access.
- Audit Trails: For accountability, permissions can be set to determine who can view the audit trails of folders, tracking every interaction.
3. File-Level Granular Permissions:
- File Listings: Users can be granted permission to only view the list of files without accessing the actual content. This is beneficial for roles that require a bird’s-eye view without deep data interaction.
- File Operations: Detailed permissions can be set for tasks like adding new files, downloading, updating, or even previewing them. This ensures that files are only modified by authorized users.
- Sharing & Audit Trails: Files can be shared individually, ensuring that only relevant data is accessible to external parties. Just like folders, the audit trails of files can be viewed based on set permissions, ensuring transparency.
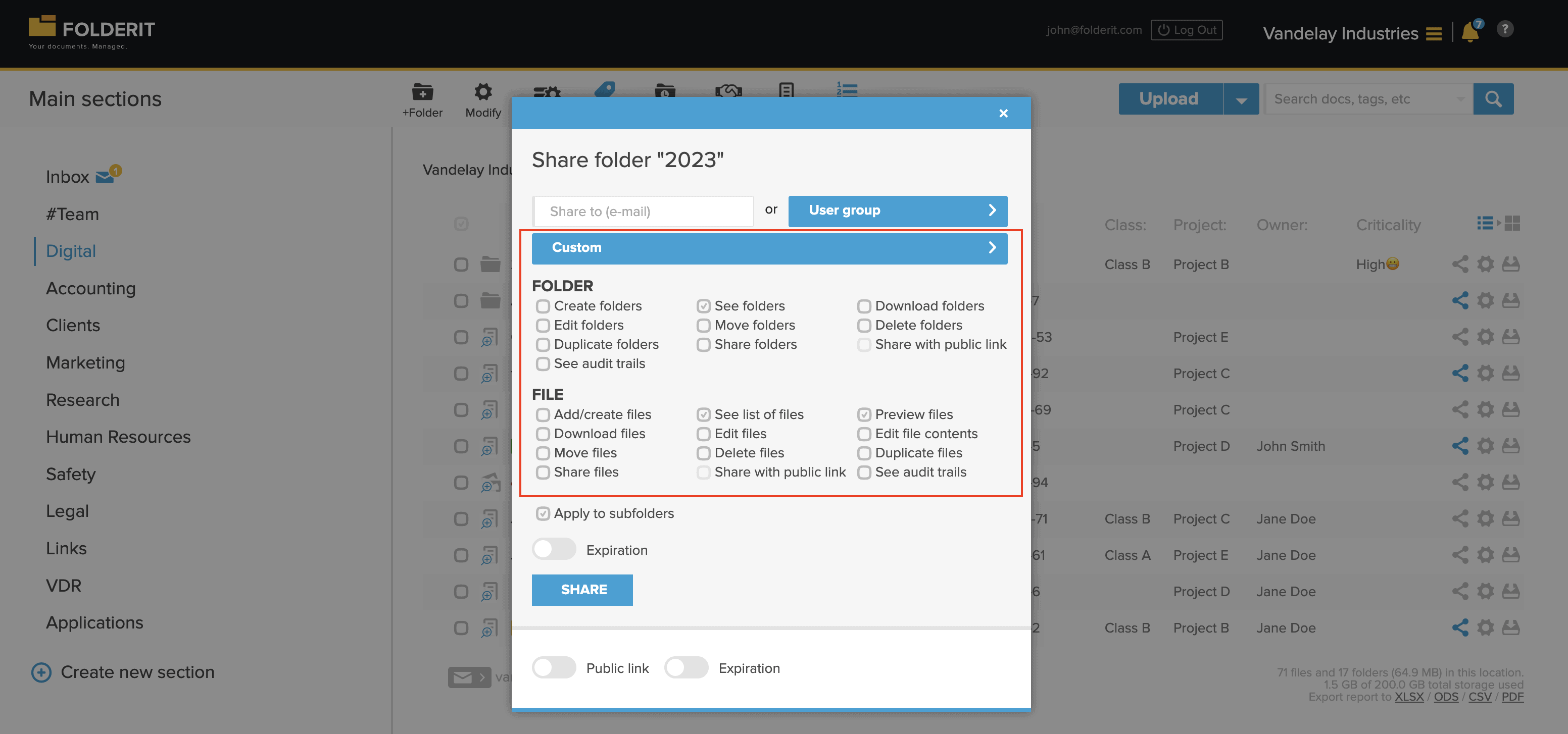
Custom permission level in Folderit DMS
4. Centralized Sharing Mechanism:
- Through a dedicated popup window, Folderit facilitates precise sharing. Users can share with specific emails or user groups, and administrators can view a detailed breakdown of shared permissions. This allows for custom permissions at the account, folder, and file levels, with an option to make permissions recursive for consistent access management.
Benefits of Implementing Custom Permission Levels in Folderit
Enhanced Data Security:
With granular access controls, you can ensure that sensitive information is only accessible to those who truly need it. This minimizes the risk of data breaches and unauthorized access.
Tailored User Experience:
Custom permissions allow you to design a user experience that’s tailored to individual roles and responsibilities. Whether it’s a manager overseeing a project or an external consultant reviewing documents, each user gets access aligned with their specific needs.
Streamlined Collaboration:
By setting precise permissions, teams can collaborate more efficiently. Members know exactly what they can view, edit, or share, eliminating confusion and potential conflicts.
Audit Trail Visibility:
For roles that require oversight, the ability to toggle the audit trail on or off means stakeholders can track document interactions, ensuring transparency and accountability.
Flexibility in Access Control:
Whether you want to grant someone the ability to only see file names or provide full access to content, Folderit’s custom permissions offer unparalleled flexibility in access management.
Efficient Resource Management:
By controlling who can upload, download, or duplicate files, you can manage your storage space more efficiently and avoid unnecessary data duplication.
Enhanced Compliance and Governance:
For industries with strict regulatory requirements, custom permissions ensure that access controls align with compliance standards, reducing the risk of non-compliance penalties.
Quick Adaptability:
As organizational roles or project requirements change, Folderit’s custom permissions can be easily adjusted to reflect those changes, ensuring continuous alignment with business needs.
Unlocking Folderit’s Custom Permissions – The Tailor Plan Advantage
Our Tailor plan by Folderit is not just another pricing tier—it’s a commitment to providing businesses with a tailored data management experience. This plan offers exclusive features, with advanced granular access management being a prime highlight, it also includes features such as custom solutions for storage volume and number of users, approval & e-signature workflows, retention automation, document numbering system, access to the Folderit API, priority support, MS Entra ID (AD) & Okta SSO, and more.
Designed for organizations that need a personalized touch to their data management strategies, the Tailor plan ensures that every data interaction is precise, secure, and efficient.
More on Folderit’s Pricing
The Future of Access Management with Folderit
Here at Folderit we understand that the devil is in the details, and with Folderit’s granular access management, those details are in your hands, precisely controlled and expertly managed.
It’s not just about safeguarding data; it’s about wielding it with precision. So, as we march forward, remember this – in a world overflowing with information, mastering the granules is mastering the game. Take the leap with Folderit!